Incident response planning: six steps for managing a cyber security breach
Discover how to react if a cyber security breach ever affects your company with this helpful six step guide. Learn how to act in response to a cyber attack, who to notify and how, and what your next steps should be.
If your business becomes the victim of a cyber security incident, it’s important to remain calm and act rapidly.
To do this, it’s vital to have a fully documented plan in place. You can base yours on the six steps outlined below.
You should also practise this plan on a regular basis, at least once a quarter, so everyone in your team knows what they are supposed to do and will be able to act as swiftly as possible.
Failing to move quickly, plus neglecting to report the incident to the right authorities and affected parties, can exacerbate the consequences of the attack, land you in legal trouble and increase the costs to your business.
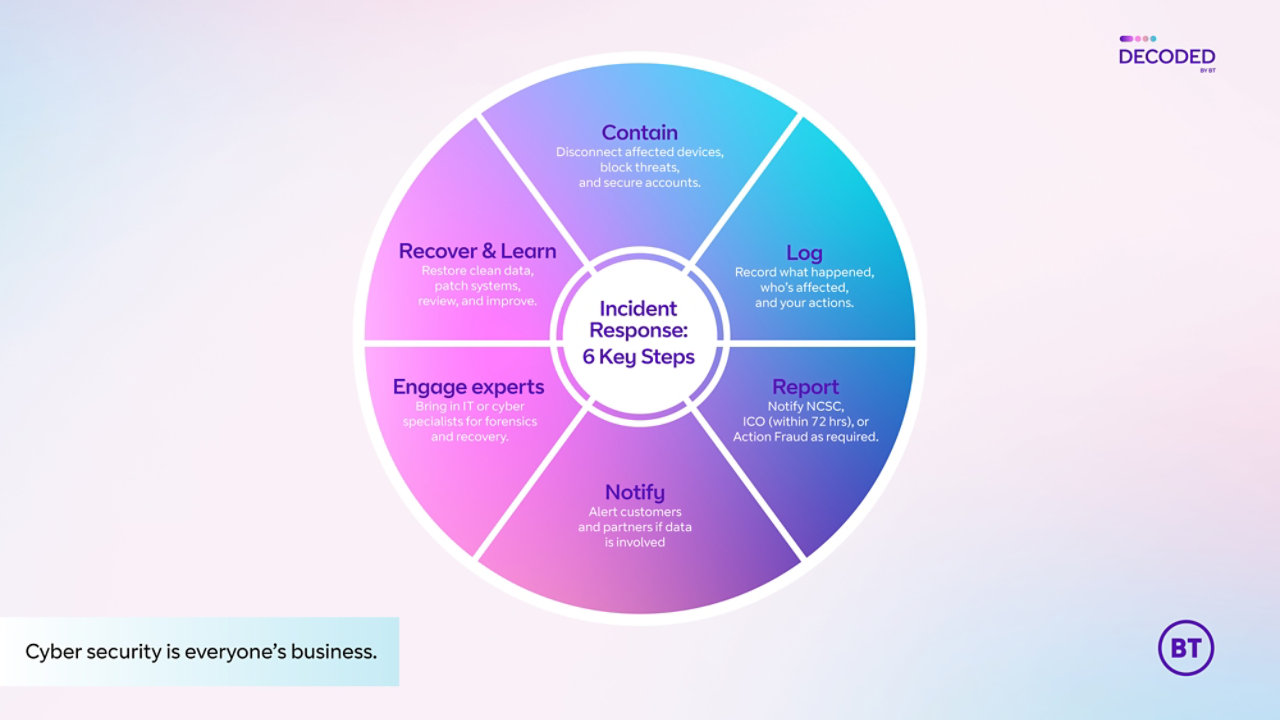
1. Make it safe and contained quickly
As soon as you suspect a problem has occurred, be sure to do the following:
- Disconnect all affected devices from the internet and your internal network (but don’t switch them off unless an expert has advised you to do so).
- Change the passwords or disable access for any accounts you think might have been compromised.
- Use your firewall to block any internet domains or addresses that you suspect may be malicious.
Your immediate aim should be to prevent the attack from spreading any further within your business, without destroying any evidence.
In the first hour of a cyberattack, your best investment is time: contain safely, capture evidence, report early. Those three actions will determine how fast you recover – and how much it costs.
2. Document everything
Immediately start an incident log and record everything that’s relevant. It should include the following information:
- Who discovered the incident.
- A timeline of what happened.
- The systems and users affected.
- The indications that these have been compromised.
- The actions you have taken.
Doing this will speed up the notifications you need to make (see step 3), as well as help to expedite any insurance claims. It’ll also improve your post-incident review (see step 6).
Depending on the kind of attack that has happened, you will need to report to at least one, but maybe all, of the following organisations:
- For significant cyber incidents, the National Cyber Security Centre (NCSC). Note that this does not replace mandatory reporting to the ICO (see below).
- If people’s personal data is involved, GDPR states that you must notify the Information Commissioner’s Office (ICO) within 72 hours.
- For fraud and cyber-crime incidents, Action Fraud (which is run by the police).
Note that the UK government does not condone making payments in the case of a ransomware incident, a policy we strongly agree with here at BT.
4. Notify customers and partners
If the cyber attack involves the loss or theft of personal data belonging to your customers, GDPR says that you must notify those affected as soon as possible.
You should also notify any other organisations that your business partners with, such as suppliers or clients, if they are also affected.
Here, it’s important to act proportionately. As part of your incident response planning, prepare a factual statement that you can send out. It should explain what happened, what you’ve done and what the people reading it should do. Above all, don’t speculate on anything you don’t know for sure, and don’t make any promises.
5. Get the right experts on board
If a company provides a managed service for your business security solutions, get them involved as soon as possible. Otherwise, find a trusted firm who can provide you with incident-management support. They’ll be able to help with forensics, containment and recovery.
6. Recover and learn
Once the dust settles, you can start to get things back up and running.
- Ensure you restore data only from clean, unaffected back-ups.
- Change all your log-in credentials.
- Patch any vulnerabilities that may have caused the incident (such as software that hadn’t been updated).
Then conduct a post-incident review to clarify what happened and how. For this to be a useful learning exercise, it should result in a set of actions, each with an owner who’s responsible for carrying it out.
An effective review will also enable you to improve your security measures and incident response plan.
Key takeaways
If you only remember three things, make them these:
- Prepare a documented incident response plan where it’s clear who needs to do what and when.
- Act rapidly as soon as you suspect a problem: respond decisively and report early.
- Hold a post-incident review to learn from what happened. Use it to help your business improve its security and incident response plan.


